The Keylime open source project is a system for verifying the integrity of remote servers, specifically cloud instances. It provides a secure method for attestation, which is the process of verifying the integrity of a system.
The Keylime project is designed to be lightweight and easy to use, with a focus on simplicity and security. It uses the Trusted Platform Module (TPM) hardware security module, which is a hardware chip that stores cryptographic keys and performs cryptographic operations, to provide secure attestation of the integrity of a system.
The Keylime project is developed and maintained by a community of volunteers and is available under an open source license. It is designed to be used by cloud providers, enterprise IT departments, and other organizations that need to verify the integrity of remote servers.
Keylime is primarily used for attesting the integrity of remote servers, specifically cloud instances. This is important because it allows organizations to ensure that the servers they are using are in a known good state, and that they have not been tampered with or compromised.
There are several specific areas where Keylime can be used:
- Cloud computing: Keylime can be used by cloud providers to verify the integrity of their servers and ensure that they are providing secure and reliable services to their customers.
- Enterprise IT: Keylime can be used by IT departments to verify the integrity of servers in their own infrastructure, including on-premises servers and servers in the cloud.
- Internet of Things (IoT): Keylime can be used to verify the integrity of IoT devices, ensuring that they are secure and have not been compromised.
- Industrial control systems: Keylime can be used to verify the integrity of industrial control systems, ensuring that they are secure and have not been compromised.
Overall, Keylime is a useful tool for any organization that needs to ensure the integrity of their servers, particularly in environments where security is a critical concern.
Here are ten examples of how Keylime could be used in real-world scenarios:
- A cloud provider uses Keylime to verify the integrity of their servers before allowing customers to spin up new instances. This helps to ensure that the servers are in a known good state and have not been tampered with.
- An enterprise IT department uses Keylime to verify the integrity of their on-premises servers before making updates or changes to them. This helps to ensure that the servers are in a known good state and have not been compromised.
- A manufacturer uses Keylime to verify the integrity of their industrial control systems before allowing them to be connected to the internet. This helps to ensure that the systems are secure and have not been compromised.
- A healthcare organization uses Keylime to verify the integrity of their servers before allowing them to be used to store and process sensitive patient data.
- A government agency uses Keylime to verify the integrity of their servers before allowing them to be used to store and process sensitive government data.
- A financial institution uses Keylime to verify the integrity of their servers before allowing them to be used to store and process financial data.
- A retailer uses Keylime to verify the integrity of their servers before allowing them to be used to process credit card transactions.
- A utility company uses Keylime to verify the integrity of their servers before allowing them to be used to control critical infrastructure, such as power plants or water treatment facilities.
- An internet service provider uses Keylime to verify the integrity of their servers before allowing them to be used to provide internet services to their customers.
- A cybersecurity company uses Keylime to verify the integrity of their servers before allowing them to be used to provide security services to their clients.
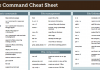
Here are ten examples of Keylime commands that could be used in various scenarios:
keylime verify: This command verifies the integrity of a remote server by performing an attestation.keylime enroll: This command enrolls a new server with Keylime, allowing it to be verified in the future.keylime unenroll: This command removes a server from the Keylime system, disabling attestation for that server.keylime create-key: This command generates a new key pair for use with Keylime.keylime activate-key: This command activates a key pair, making it ready for use with Keylime.keylime deactivate-key: This command deactivates a key pair, disabling it for use with Keylime.keylime trust-ca: This command trusts a new certificate authority (CA) for use with Keylime.keylime untrust-ca: This command removes a certificate authority (CA) from the list of trusted CAs for use with Keylime.keylime register-manifest: This command registers a new manifest with Keylime, which specifies the expected state of a server.keylime unregister-manifest: This command removes a manifest from the Keylime system, disabling attestation for servers with that manifest.